Telecommunications
Your network runs 24/7. Your development shouldn't stop either
AI agents that understand telecom - from COBOL billing to 5G orchestration.
Trusted by engineers at
Why Leading Telcos Choose Zencoder
The only AI platform built for telecom's unique challenges: vendor lock-in, legacy debt, and innovation speed.
-
100% On-Premise
-
Your subscriber data never leaves your data center. Deploy in your NOC, air-gapped if needed.
-
Policy-Driven Development
-
Transform compliance documents into automated code reviews. Every commit verified.
-
Accelerate Without Risk
-
Generate production code and tests for systems that can't fail. Five-nines reliability maintained.
Solutions
Transform what holds you back. Build what sets you apart.
Code Generation for Telecom Systems
Generate new features and integrations for BSS/OSS systems. Modern implementation, your business logic preserved.
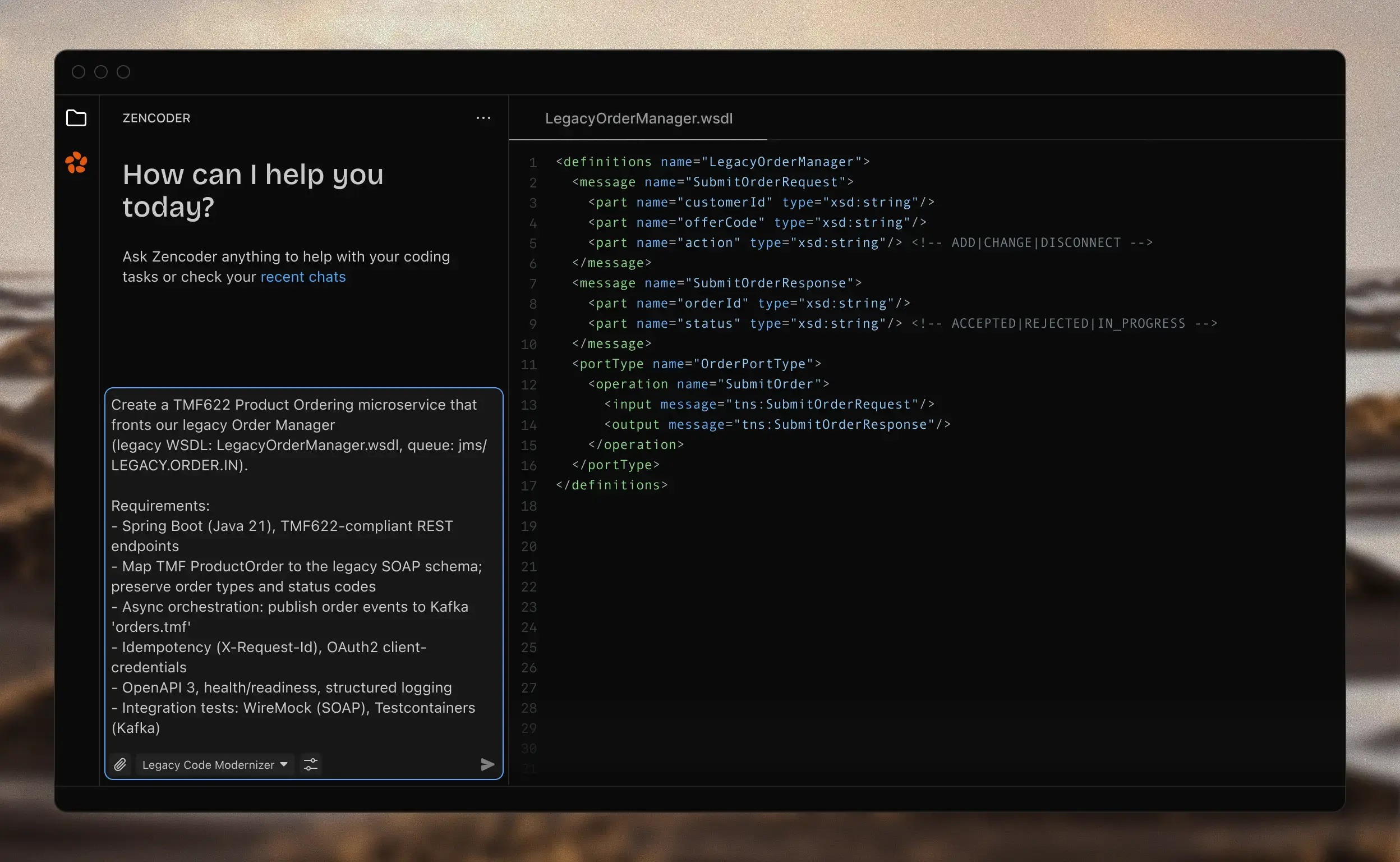
- Industry-aware code generation
- Understands rating, mediation, provisioning patterns.
- Multi-language fluency
- COBOL to Python, Java to Go, all production-ready.
- Integration-ready code
- Pre-built adapters for your existing systems.
Automated Testing with Zentester
Generate comprehensive test suites for mission-critical telecom systems.
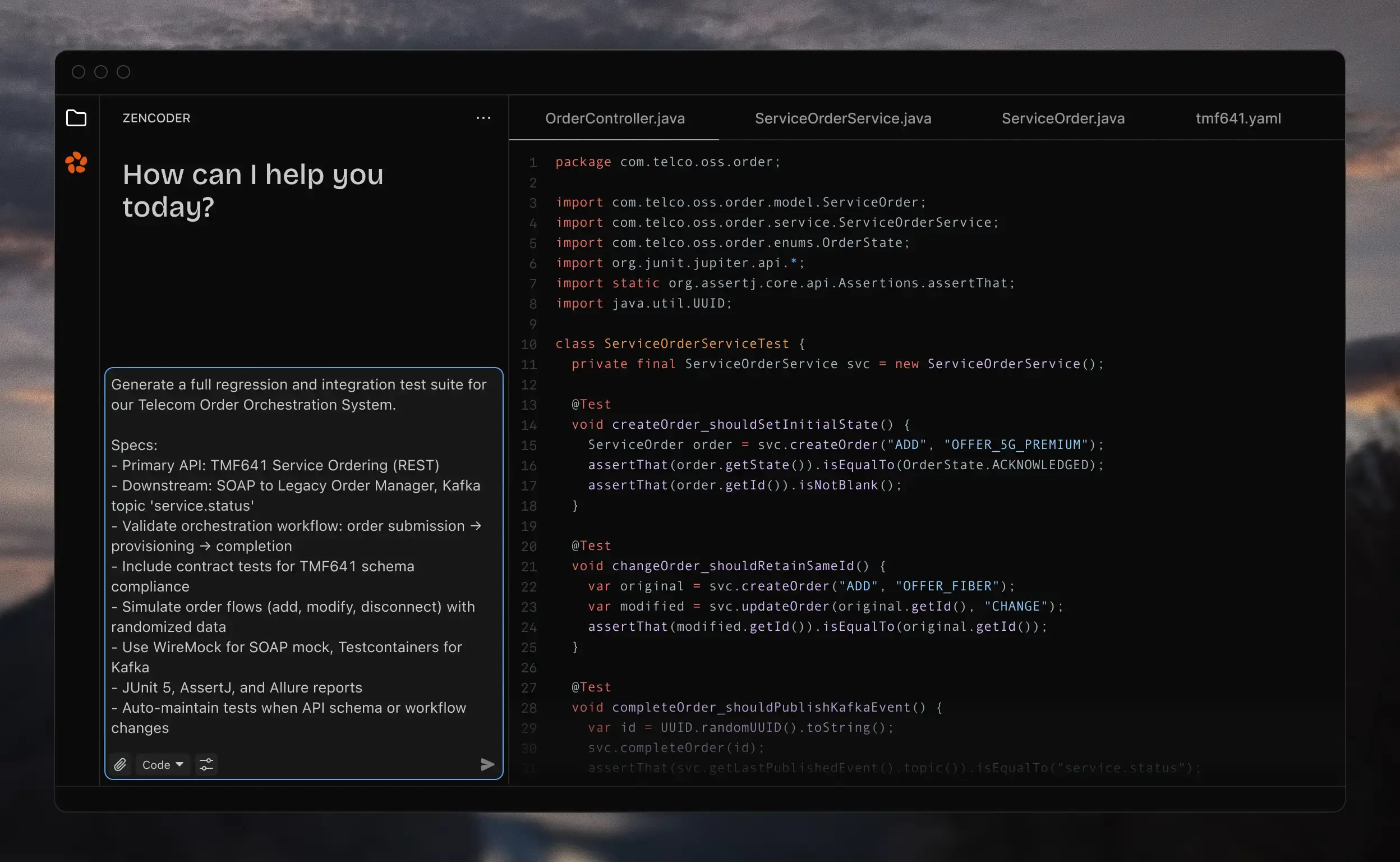
- Five-nines testing
- Test cases for 99.999% uptime requirements.
- Protocol validation
- SS7, Diameter, SIP, REST interface testing.
- Regression protection
- Ensure changes don't impact critical paths.
Compliance & Code Review Automation
Transform compliance documents and security policies into automated code reviews. Every commit checked, every standard enforced.
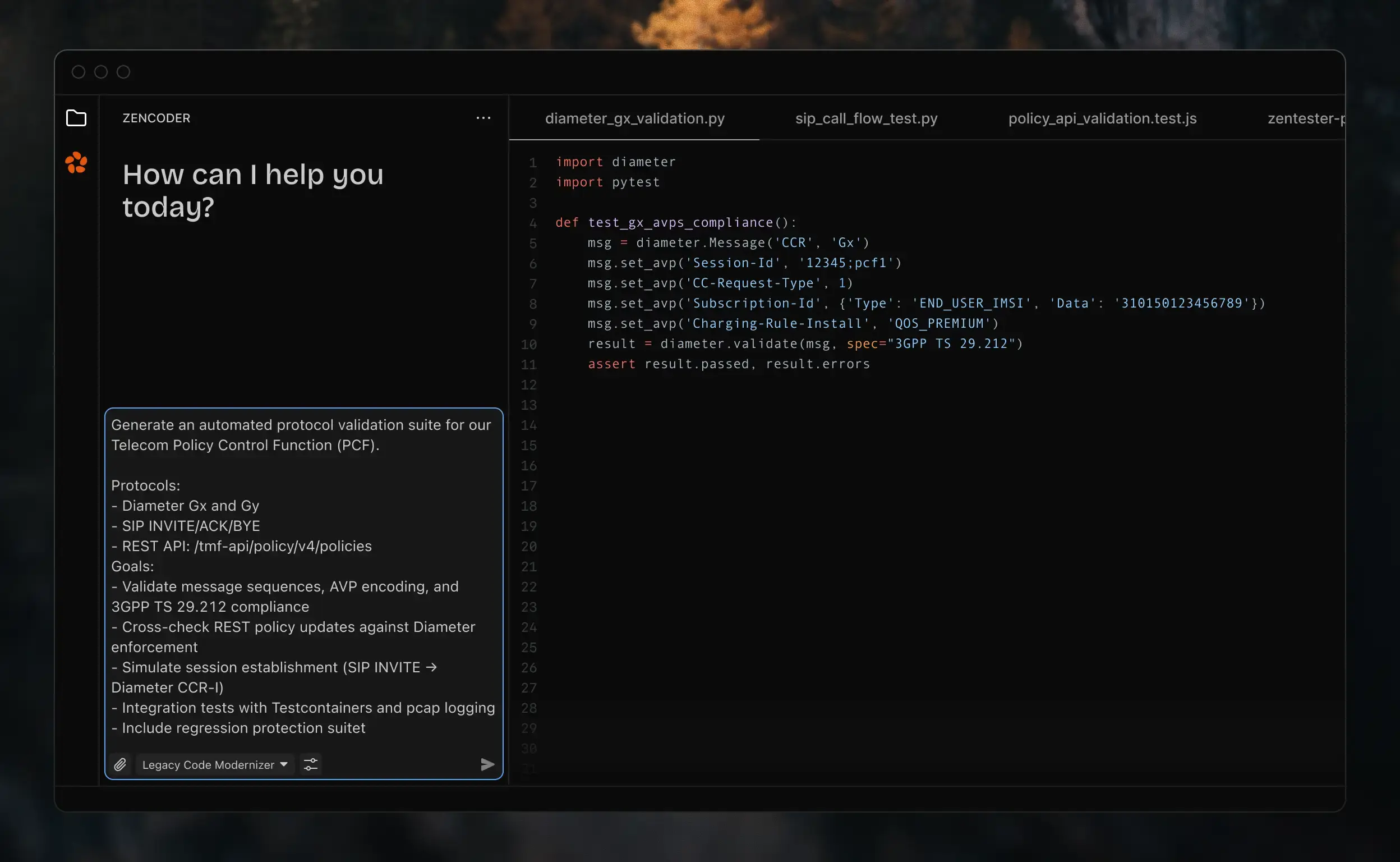
- Policy as code
- Convert compliance documents into automated checks.
- Security scanning
- Telecom-specific vulnerabilities and OWASP compliance.
- Complete audit trail
- Every review logged, every decision documented.
BUILT FOR TELECOM REALITY
How we stack up against your alternatives
Stop choosing between expensive SIs and risky in-house development.
| Features | Zencoder | SYSTEM INTEGRATORS | GENERIC AI TOOLS |
|---|---|---|---|
| On-premise option |
Included
Yes: Included
|
Expensive
Yes: Expensive
|
✕ |
| Compliance |
Automated policy enforcement
Yes: Automated policy enforcement
|
Document heavy | No awareness |
| Multi-vendor support |
Automated
Yes: Automated
|
Manual integration
Yes: Manual integration
|
✕ Single vendor |
| Testing approach |
Unit and E2E Testing
Yes: Unit and E2E Testing
|
Manual test plans | ✕ Modern only |
| Code ownership |
100% your IP
Yes: 100% your IP
|
Often retained | Your IP at risk |
| Cost | $49-119/developer | $10M+ projects | $1M+ licenses |
Zen agents
Pre-Built Agents
Start with pre-configured agents that understand telecom, or create custom agents for your specific needs.
Security Auditor
Identifies vulnerabilities in telecom systems ensuring compliance with industry standards and protecting against cyber threats.
Performance Optimizer
Enhances code efficiency for real-time network operations reducing latency and improving service quality metrics.
Legacy Code Modernizer
Updates decades-old telecom infrastructure code without disrupting critical network operations and customer services.
Infrastructure as Code Specialist
Creates IaC configurations for network functions virtualization and cloud-native telecom deployments.
DevOps Pipeline Builder
Builds CI/CD pipelines for rapid deployment of network features while maintaining five-nines uptime requirements.
Architecture Designer
Creates architectures for 5G and edge computing systems handling millions of connected devices and IoT endpoints.
Integrations
Integrations to amplify your workflow
Connect your favorite tools and services to create a seamless workflow.
SECURITY
On-premise by default. Secure by design.
Enterprise security without enterprise complexity. Fast deployment, total control.
-
On-Premise Deployment
- Deploy entirely within your infrastructure. No cloud dependencies, no external calls.
-
Air-Gapped Ready
- Full functionality without internet. Updates via secure media. Zero external access.
-
SOC 2 Type II Certified
- Annual third-party validation. Full audit reports available for your compliance team.
-
Zero Data Retention
- Each session is ephemeral. No training on your data. Complete proprietary protection.
-
Complete Audit Trails
- Immutable logs for all actions. Export ready for regulatory reviews and audits.
-
??
- AES-256 at rest and in transit. HSM integration. Certificate-based authentication.